ISO 27001 Management System A Secure Foundation
The ISO 27001 management system provides a structured approach to information security. It’s more than just a set of rules; it’s a comprehensive framework for identifying, assessing, and mitigating risks to your data. Implementing this system leads to a more secure environment, reduced vulnerabilities, and ultimately, greater trust from stakeholders.
This system articulates the crucial stages from initial risk assessment to ongoing maintenance, highlighting the importance of continuous improvement in today’s dynamic threat landscape. Understanding the different types of controls, from technical to administrative, and the procedures for implementing them are key aspects covered.
Introduction to ISO 27001 Management System
ISO 27001 is a globally recognized standard for establishing and maintaining an Information Security Management System (ISMS). It provides a framework for organizations to identify, assess, and mitigate information security risks. The purpose is to protect sensitive information assets, ensure business continuity, and build trust with stakeholders. Compliance with ISO 27001 demonstrates a commitment to robust information security practices.
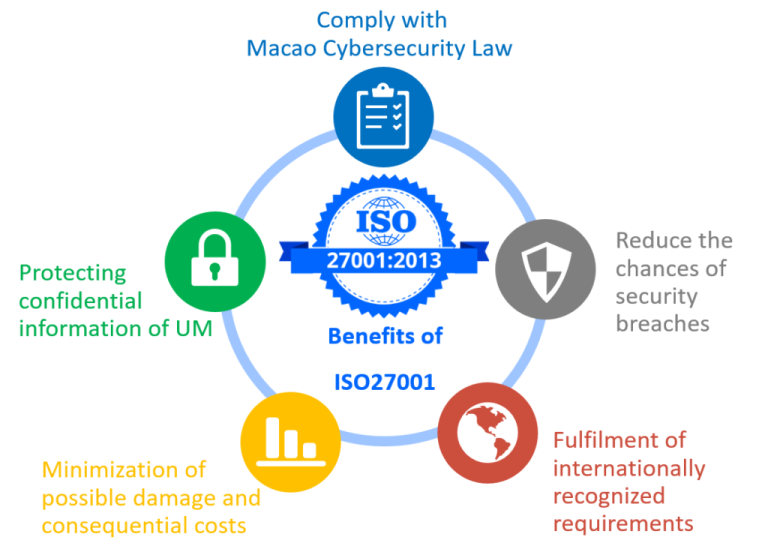
Implementing an ISO 27001 management system offers substantial benefits. Organizations gain a structured approach to information security, reducing vulnerabilities and improving overall security posture. This, in turn, fosters trust with customers, partners, and investors, leading to increased confidence and potentially higher profitability. Furthermore, a documented and regularly reviewed ISMS minimizes the risk of costly security breaches.
Key Benefits of Implementing ISO 27001
The benefits extend beyond mere compliance. A robust ISMS enhances operational efficiency by streamlining processes and reducing redundancies. It also facilitates proactive risk management, preventing potential threats before they impact operations. This results in reduced operational downtime, minimizing financial losses. Additionally, ISO 27001 fosters a culture of security awareness, empowering employees to contribute to the overall security of the organization’s assets.
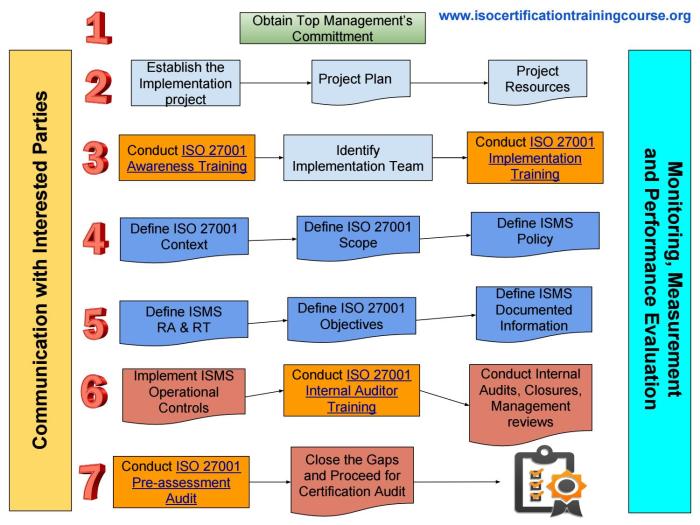
Stages Involved in Implementing an ISO 27001 Management System
Implementing an ISO 27001 management system involves a phased approach, typically comprising these steps:
- Planning and Assessment: This phase involves defining the scope of the ISMS, assessing the current security posture, and defining the organization’s security objectives. This initial step is crucial for ensuring the system aligns with the organization’s specific needs and risks.
- Policy and Procedure Development: Developing comprehensive policies and procedures, outlining the roles and responsibilities of personnel, is essential. Clear guidelines prevent ambiguity and promote consistent security practices across the organization.
- Risk Assessment and Treatment: A thorough risk assessment is conducted to identify potential vulnerabilities and threats. Appropriate risk treatment strategies are developed and implemented to minimize the impact of identified risks. This step directly addresses the organization’s unique exposure.
- Implementation of Controls: Based on the risk assessment, security controls are implemented to mitigate identified risks. This step involves choosing and implementing security measures tailored to the organization’s specific context and risks.
- Monitoring and Review: The ISMS must be continuously monitored and reviewed to ensure its effectiveness and relevance. Regular reviews allow for adaptations to changing business needs and emerging threats. This iterative process ensures long-term effectiveness.
- Certification: Following successful implementation and internal audits, the organization can seek certification from a recognized certification body. This final step validates the organization’s commitment to robust information security.
Components of an ISO 27001 Management System
The ISO 27001 standard Artikels key components of an ISMS. These components form the foundation of a robust and effective security management system.
| Component | Description | Example |
|---|---|---|
| Information Security Policy | Defines the organization’s commitment to information security and articulates the overall approach. | A statement outlining the organization’s commitment to protecting sensitive information and adhering to legal and regulatory requirements. |
| Risk Assessment | Identifies and analyzes potential threats and vulnerabilities. | Identifying potential data breaches, unauthorized access, and system failures. |
| Security Controls | Measures and actions to mitigate identified risks. | Implementing strong passwords, firewalls, and intrusion detection systems. |
| Incident Management | Processes for detecting, responding to, and recovering from security incidents. | Defining procedures for handling data breaches, cyberattacks, and other security incidents. |
| Monitoring and Review | Regular evaluation of the ISMS to ensure its effectiveness. | Regular security audits, system penetration testing, and security awareness training. |
Risk Management in ISO 27001

Source: co.uk
Risk management is a critical component of any robust information security management system, and ISO 27001 places significant emphasis on it. Effective risk management helps organizations proactively identify, assess, and mitigate potential threats to their information assets. This approach fosters a culture of security awareness and preparedness, minimizing the likelihood and impact of security breaches.
Risk assessment, a cornerstone of ISO 27001, is a structured process that aims to identify, analyze, and evaluate potential information security risks. This involves systematically examining potential threats, vulnerabilities, and their potential impact on organizational operations. The outcome of this assessment informs the development of appropriate risk treatment strategies.
Risk Identification, Analysis, and Evaluation
Identifying potential information security risks involves a comprehensive review of various factors, including internal weaknesses, external threats, and emerging trends. Analyzing these risks entails determining the likelihood of their occurrence and the potential impact on organizational operations and assets. Evaluating risks involves prioritizing them based on their likelihood and impact, using a qualitative or quantitative approach, to determine their significance. This process requires collaboration among various stakeholders to gather diverse perspectives and ensure a holistic view of potential risks.
Risk Treatment Strategies
Effective risk treatment strategies are essential to mitigating identified risks. These strategies involve various actions aimed at reducing the likelihood of a risk event occurring or minimizing the impact if it does occur.
| Strategy | Description | Applicability | Example |
|---|---|---|---|
| Avoidance | Eliminating the risk by removing the activity or asset that is exposed to it. | Suitable for high-impact, high-likelihood risks where alternatives exist. | Discontinuing a service with known security vulnerabilities. |
| Mitigation | Reducing the likelihood or impact of the risk through preventative or detective controls. | Appropriate for most risks. | Implementing multi-factor authentication to mitigate the risk of unauthorized access. |
| Transfer | Shifting the ownership of the risk to another party, such as through insurance. | Useful for risks that can be transferred without significant operational changes. | Purchasing cyber insurance to transfer the financial risk of a security breach. |
| Acceptance | Acknowledging the risk and accepting its potential impact. | Suitable for low-impact, low-likelihood risks where the cost of mitigation outweighs the potential loss. | Accepting a low-probability risk of data loss due to a minor software glitch. |
| Termination | Eliminating the risk by ceasing the activity or removing the asset. | Applicable for risks that are deemed unacceptable, especially when there are no viable alternatives. | Stopping a project with severe security risks, even if other projects are in progress. |
Categorization of Information Security Risks
Categorizing information security risks facilitates focused risk management efforts. One method involves grouping risks based on asset type (e.g., customer data, financial records), threat source (e.g., internal, external), and potential impact (e.g., financial loss, reputational damage). Another approach might classify risks according to their likelihood of occurrence and the potential damage they could cause, using a matrix approach. Consistent categorization enables efficient prioritization and targeted mitigation efforts.
Controls and Implementation in ISO 27001

Implementing an effective Information Security Management System (ISMS) hinges on the robust application of controls. These controls act as the mechanisms for mitigating identified risks and ensuring the security of organizational information assets. A well-structured control framework provides a clear roadmap for achieving compliance with ISO 27001 and fosters a secure environment for operations.
Role of Controls in Managing Information Security Risks
Controls play a crucial role in managing information security risks by reducing the likelihood and impact of threats. They address vulnerabilities by implementing preventative, detective, and corrective measures. By establishing and maintaining these controls, organizations can effectively safeguard their sensitive data and operational processes.
Types of Security Controls
Security controls are broadly categorized into three main types: technical, administrative, and physical. Understanding the distinctions between these types is vital for developing a comprehensive security strategy.
- Technical Controls: These controls rely on technological solutions to safeguard information. They encompass various measures like firewalls, intrusion detection systems, encryption, access controls, and antivirus software. Technical controls often automate security tasks and can be highly effective in preventing unauthorized access and data breaches.
- Administrative Controls: These controls focus on policies, procedures, and processes related to information security. Examples include security awareness training, incident response plans, access control policies, and security audits. Administrative controls establish the framework for managing and enforcing security policies within the organization.
- Physical Controls: These controls protect physical assets that house information systems and data. They include security measures like controlled access to facilities, surveillance systems, environmental controls (e.g., climate control), and physical security devices (e.g., locks, alarms). Physical controls ensure the physical security of infrastructure and data.
Examples of Control Measures for Specific Information Security Risks
To illustrate the application of controls, consider the risk of unauthorized access to sensitive customer data. A combination of controls could be implemented. For example, a strong password policy (administrative), multi-factor authentication (technical), and regular security audits (administrative) can be combined to mitigate this risk.
Table of Common Information Security Controls
| Control | Description | Example |
|---|---|---|
| Access Control | Defines and enforces rules for who can access what data and systems. | Strong passwords, multi-factor authentication, role-based access control. |
| Data Encryption | Transforms data into an unreadable format to protect it from unauthorized access. | Encrypting sensitive data at rest and in transit. |
| Security Awareness Training | Educates employees about information security threats and best practices. | Regular training sessions on phishing, social engineering, and password management. |
| Incident Response Plan | Artikel’s procedures for responding to security incidents. | Documented procedures for detecting, containing, and recovering from security breaches. |
| Vulnerability Management | Identifies and addresses security vulnerabilities in systems and applications. | Regular vulnerability scans and penetration testing. |
Procedure for Implementing a Security Control
Implementing a security control requires a structured approach. A typical procedure involves:
- Assessment: Analyze the need for the control, evaluate the current situation, and identify the appropriate control. Assess the existing security posture to determine the suitability of the proposed control.
- Planning: Define the scope, resources, timelines, and responsibilities for implementing the control. This includes developing a detailed plan for execution and outlining the necessary resources.
- Implementation: Execute the plan, ensuring proper configuration and testing of the control. This step requires meticulous attention to detail and adherence to established procedures.
- Verification: Validate that the control is operating as intended and that the desired security outcomes are achieved. This phase is critical for confirming the effectiveness of the implemented control.
- Monitoring: Regularly monitor the control to ensure ongoing effectiveness. Continuously review the effectiveness of the control and make necessary adjustments as needed.
Maintaining and Improving ISO 27001 Management System

Maintaining a robust ISO 27001 Information Security Management System (ISMS) requires continuous effort and adaptation to evolving threats and business needs. A static system will quickly become ineffective in safeguarding an organization’s sensitive data and operations. This section details the crucial aspects of ongoing monitoring, review, and improvement for a thriving ISMS.
The success of an ISO 27001 implementation hinges significantly on its ongoing management and improvement. This proactive approach ensures that the system remains aligned with the organization’s current context, effectively mitigating risks and maximizing its effectiveness in safeguarding valuable assets.
Importance of Ongoing Monitoring and Review
Regular monitoring and review are essential to assess the continued effectiveness of the ISO 27001 ISMS. This process involves consistently evaluating the controls’ performance, identifying any gaps, and ensuring the system remains aligned with the organization’s evolving needs and risks. Monitoring and review processes help prevent security breaches, maintain compliance, and demonstrate a commitment to information security.
Role of Metrics and Performance Indicators
Metrics and performance indicators are crucial for objectively evaluating the effectiveness of the ISO 27001 ISMS. Quantifiable data provides valuable insights into the system’s performance and allows for targeted improvements. Tracking key metrics helps identify trends, pinpoint areas needing attention, and demonstrate the system’s value to stakeholders.
Process of Continuous Improvement
Continuous improvement is a fundamental aspect of any successful ISO 27001 ISMS. It involves a systematic approach to identifying areas for enhancement, implementing changes, and evaluating their impact. This iterative process ensures that the system remains adaptable to emerging threats and evolving business needs. Regular audits, feedback mechanisms, and lessons learned from incidents are vital elements of this continuous process.
Common Metrics for Assessing ISO 27001 Performance
| Metric | Description | Measurement Method |
|---|---|---|
| Security incidents | Number of security incidents reported | Tracking system, incident reports |
| Vulnerability assessments | Number of vulnerabilities identified and addressed | Automated vulnerability scanning tools, penetration testing reports |
| Compliance with controls | Percentage of controls meeting defined requirements | Control checklists, self-assessments |
| Data breaches | Number of data breaches and their impact | Incident reports, data loss prevention tools |
| Employee training completion rate | Percentage of employees completing required security training | Training records, completion certificates |
| Time to resolve security incidents | Average time taken to resolve security incidents | Incident tracking system |
Process for Updating and Maintaining the ISO 27001 System, Iso 27001 management system
A structured process for updating and maintaining the ISO 27001 system is crucial for long-term effectiveness. This process should encompass the following:
- Regular review of the risk assessment to ensure it remains current and reflects the organization’s evolving context.
- Periodic review and updating of the documented information security policies, procedures, and controls.
- Regular monitoring of the effectiveness of the implemented controls and associated performance indicators.
- Implementation of corrective actions to address identified weaknesses and gaps in the system.
- Review and update the system based on lessons learned from security incidents, audits, and external factors.
This cyclical process ensures that the system adapts to new threats and vulnerabilities and maintains its effectiveness in protecting sensitive data and assets. Regular internal audits and external assessments can provide crucial feedback for improvement and compliance.
Wrap-Up
In conclusion, a robust ISO 27001 management system is vital for organizations looking to proactively safeguard their information assets. By systematically addressing risk management, implementing effective controls, and fostering a culture of continuous improvement, organizations can significantly enhance their security posture. This framework empowers them to not only meet compliance requirements but also build a more resilient and trustworthy operation.