ISO 27001 Certification Services Secure Your Future
ISO 27001 certification services provide a roadmap for organizations to bolster their information security posture. This comprehensive approach articulates a structured process for achieving robust security, demonstrating a commitment to data protection and compliance. By understanding the intricacies of ISO 27001, organizations can significantly reduce risks and enhance their reputation. Navigating the certification process can be complex, but expert guidance from qualified providers can streamline the journey.
The services offered encompass various aspects, from initial assessments to ongoing support. Different service packages cater to specific needs and budgets. This guide explores the key elements of ISO 27001 certification, highlighting the benefits, challenges, and essential considerations for selecting a suitable service provider.
Introduction to ISO 27001 Certification Services
Source: isu.pub
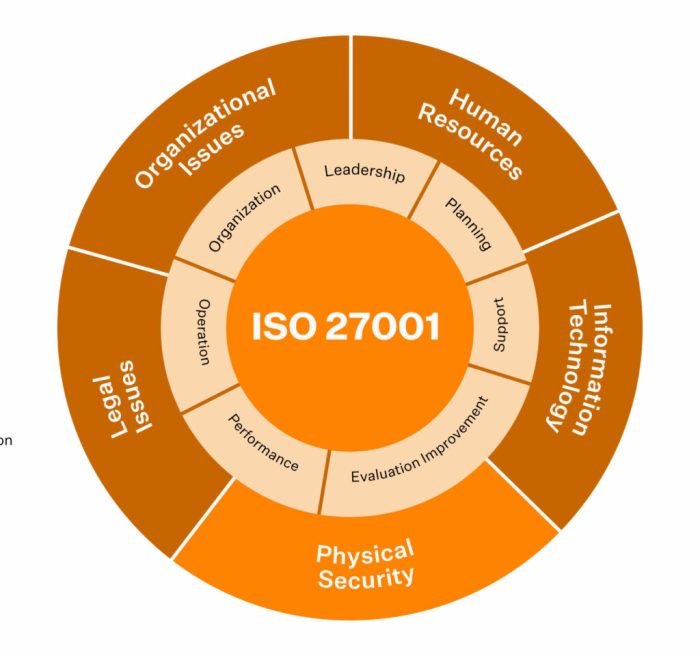
ISO 27001 is a globally recognized standard for information security management systems (ISMS). It provides a framework for organizations to identify, assess, and mitigate information security risks. This framework is the best practice for protecting sensitive data and ensuring the confidentiality, integrity, and availability of information assets. Adherence to ISO 27001 demonstrates a commitment to robust information security practices, enhancing trust with stakeholders.
The ISO 27001 certification process involves a rigorous assessment of an organization’s existing information security controls and procedures. A certified third-party auditor evaluates the organization’s adherence to the standard. Successful implementation and demonstration of the controls and processes lead to certification, which is valid for a specified period.
Process of Achieving ISO 27001 Certification
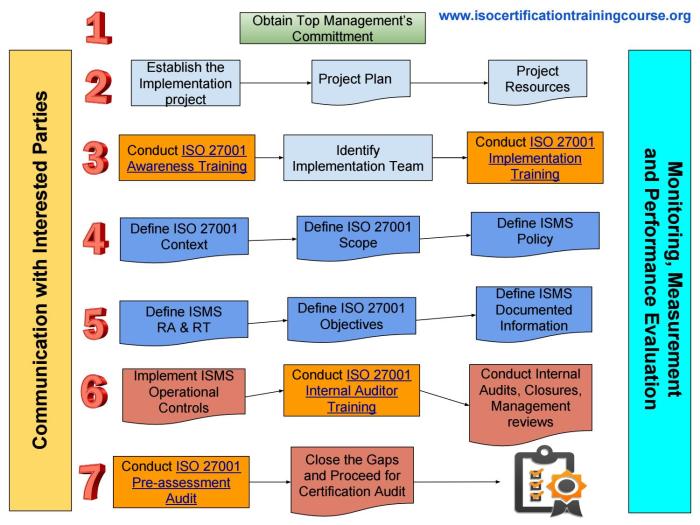
The certification process typically involves several key stages. First, organizations develop and implement an Information Security Management System (ISMS) based on the ISO 27001 standard. This often involves defining policies, procedures, and controls and documenting them. Next, they must demonstrate the effectiveness of their ISMS through internal audits and self-assessments. Then, an external auditor conducts a thorough review of the organization’s ISMS to ensure it meets the requirements of ISO 27001. The successful completion of this audit leads to certification.
Benefits of ISO 27001 Certification
Organizations benefit from ISO 27001 certification in numerous ways. Firstly, it enhances their reputation for security and trust, making them more attractive to clients and partners. Secondly, it reduces the risk of data breaches and associated financial losses. Robust security controls implemented as part of the certification process contribute significantly to this reduction. Thirdly, it fosters a culture of information security awareness within the organization. Finally, it provides a framework for continuous improvement, allowing organizations to adapt to evolving security threats and maintain a strong security posture.
Comparison of ISO 27001 Certification Service Providers
Choosing the right certification body is crucial for a successful ISO 27001 certification journey. The table below provides a preliminary comparison of potential service providers, highlighting their offerings, pricing, and client feedback. This table provides a starting point for organizations seeking certification services.
| Provider | Services Offered | Pricing | Reviews |
|---|---|---|---|
| Example Provider 1 | Comprehensive ISO 27001 certification services, including gap analysis, documentation, training, and ongoing support. | Competitive pricing and tailored packages are available. | Positive reviews highlighting excellent communication and responsive support. |
| Example Provider 2 | Expert guidance through the entire certification process, including tailored recommendations and support for specific industry requirements. | Transparent pricing structure, clear breakdown of costs. | Client testimonials emphasize the provider’s deep expertise and practical approach. |
Types of ISO 27001 Certification Services
ISO 27001 certification, a globally recognized standard for information security management systems (ISMS), requires a structured approach. Various services are available to support organizations in achieving and maintaining this certification. These services cater to different needs and stages of the certification journey.
A comprehensive understanding of these services allows organizations to choose the most appropriate package for their specific circumstances. Different service providers offer varying service packages, reflecting their unique expertise and the specific needs of diverse organizations. Careful evaluation of these packages is crucial to selecting the best fit.
Gap Analysis Services
Gap analysis services assess the current state of an organization’s information security controls against the requirements of ISO 27001. This crucial initial step identifies areas where the organization’s practices are deficient or need improvement. The process typically involves a detailed review of existing policies, procedures, and controls. The findings highlight the discrepancies between the current practices and the ISO 27001 standards, providing a clear roadmap for improvement. This enables organizations to prioritize their efforts effectively and allocate resources strategically.
Implementation Services
Implementation services provide comprehensive support in building or enhancing an ISMS compliant with ISO 27001. This encompasses developing policies, procedures, and documentation necessary to establish an effective ISMS framework. This often includes training staff on new procedures and controls, ensuring a smooth transition. Specific implementation support can range from assisting with the creation of security policies to the establishment of a robust risk management framework. The level of support tailored to the specific needs of the organization is crucial.
Audit Services
Audit services are vital for maintaining ongoing compliance with ISO 27001. These services involve a systematic assessment of the organization’s ISMS against the requirements of the standard. External audits are conducted by certified auditors who assess the organization’s controls, processes, and documentation. Internal audits can also be performed by trained personnel to monitor compliance within the organization continuously. Regular audits ensure the effectiveness and suitability of the ISMS, allowing organizations to adapt to changing threats and regulatory requirements. The frequency and scope of audits are determined by the organization’s needs and the requirements of ISO 27001.
ISO 27001 Certification Service Options
| Service Type | Description | Target Audience | Key Features |
|---|---|---|---|
| Gap Analysis | Identifies gaps between current security practices and ISO 27001 requirements. | Organizations seeking certification or wanting to assess their current security posture. | Detailed assessment of existing controls, documentation review, and identification of improvement areas. |
| Implementation | Develops and implements an ISMS compliant with ISO 27001. | Organizations starting from scratch or needing significant enhancements to their existing security framework. | Development of policies, procedures, documentation, staff training, and risk management framework establishment. |
| Audits | Evaluate the effectiveness and compliance of the ISMS against ISO 27001 requirements. | Organizations holding ISO 27001 certification or striving to maintain compliance. | External or internal audits, documentation review, control testing, reporting. |
Essential Components of ISO 27001 Certification Services

A comprehensive ISO 27001 certification service goes beyond simply assessing compliance; it provides a structured approach to building a robust information security management system (ISMS). This involves a detailed understanding of the organization’s specific needs and risks, tailoring the certification process to ensure its effectiveness and long-term value.
These services encompass a range of activities designed to not only achieve certification but also to embed a culture of information security within the organization. This fosters a proactive approach to risk management, enabling the organization to adapt to evolving threats and maintain a high level of security posture.
Risk Assessment and Gap Analysis
Thorough risk assessment is fundamental to developing an effective ISMS. This involves identifying potential threats, vulnerabilities, and impacts on the organization’s operations. A comprehensive gap analysis then compares the organization’s existing security controls against the requirements of ISO 27001. This process highlights areas needing improvement, enabling targeted enhancements and minimizing potential vulnerabilities. By understanding the specific security gaps, organizations can prioritize their efforts and allocate resources effectively, ensuring a focused and efficient implementation of security controls.
Policy Development and Implementation
Developing and implementing a comprehensive information security policy is crucial. This policy defines the organization’s commitment to information security, outlining responsibilities and procedures. Implementing the policy across the organization ensures consistency and adherence to security standards. Clear communication and training are essential components to ensure effective policy implementation and embed security awareness throughout the organization. This proactive approach fosters a security-conscious culture, minimizing the risk of human error and enhancing overall security posture.
Documentation and Procedures
Detailed documentation of the ISMS is vital for demonstrating compliance. This includes documenting policies, procedures, processes, and controls. Clear and well-structured documentation facilitates audits, both internal and external, allowing for transparency and verification of security controls. Furthermore, this documentation serves as a valuable reference for employees, enabling them to understand their roles and responsibilities in maintaining information security. The organization can benefit from a well-documented ISMS, facilitating easy audits and a clear understanding of responsibilities.
Internal Audits and Management Reviews
Regular internal audits and management reviews are crucial to monitor the effectiveness of the ISMS. These assessments identify any deviations from the established policies and procedures, enabling timely corrective actions. The management reviews provide an opportunity for the organization to assess the overall performance of the ISMS and make necessary adjustments. This continuous improvement approach ensures that the ISMS remains relevant and effective in addressing emerging threats and vulnerabilities. Internal audits act as a self-assessment tool, providing valuable insights into areas needing improvement and proactively addressing any emerging risks.
External Audit and Certification
The final stage involves the external audit and certification process. A qualified certification body conducts a thorough audit to verify the organization’s compliance with ISO 27001. Successful completion of this audit leads to the coveted ISO 27001 certification, signifying the organization’s commitment to robust information security practices. This process validates the effectiveness of the implemented security controls and ensures that the organization operates according to recognized international standards.
Table: Sequence of Activities in ISO 27001 Certification
| Step | Activity | Timeline | Resources Required |
|---|---|---|---|
| Step 1 | Risk Assessment and Gap Analysis | 2-4 weeks | Security personnel, relevant documentation, IT infrastructure access |
| Step 2 | Policy Development and Implementation | 2-4 weeks | Management commitment, policy writers, training materials |
| Step 3 | Documentation and Procedures | 2-4 weeks | Documentation specialists, templates, software for documentation management |
| Step 4 | Internal Audits and Management Reviews | Ongoing | Internal audit team, management, and relevant staff |
| Step 5 | External Audit and Certification | 2-4 weeks | Certification body, audit team, supporting documentation |
Key Considerations for Selecting a Service Provider
Choosing the right ISO 27001 certification service provider is crucial for a successful certification process. A reputable provider with a proven track record can significantly impact the outcome, ensuring a smooth and efficient journey. Selecting a provider with the necessary expertise and experience is vital to achieving compliance and maximizing the benefits of certification.
Selecting a service provider for ISO 27001 certification involves careful evaluation of several factors. The provider’s understanding of the specific industry and business context, along with their demonstrable experience in handling similar projects, directly influences the success of the certification process. Moreover, a provider’s ability to tailor their approach to the unique requirements of the organization is a key element to consider.
Experience and Expertise
Demonstrated experience in ISO 27001 certification is a critical factor. Providers with a history of successful projects and a deep understanding of the standard’s intricacies are better equipped to navigate the complexities of the certification process. This includes understanding the nuances of various industry sectors and tailoring the approach accordingly. Expert knowledge of the standard ensures that the organization’s security controls are aligned with best practices. It is crucial to look for a provider who understands not only the technical aspects but also the practical implementation and management of the security controls within the organization.
Reputation and Qualifications
A provider’s reputation speaks volumes about their reliability and competency. Positive testimonials and reviews from previous clients offer valuable insights into their service quality and commitment to client satisfaction. A provider’s certifications and accreditations, such as ISO 19011 or similar professional qualifications, provide further assurance of their expertise and adherence to best practices. In addition to their certifications, their involvement in industry associations or relevant publications demonstrates a commitment to staying abreast of evolving standards and best practices.
Comparison of Service Providers
Comparing potential service providers based on their qualifications and methodologies is essential. A comprehensive evaluation should consider the provider’s expertise in specific industry sectors, their experience with similar organizations, and their demonstrated ability to effectively manage the certification process. Evaluating their methodologies, including their approach to risk assessment, control implementation, and documentation, is also vital to ensuring a suitable fit with the organization’s requirements.
Provider Qualification Table
The following table provides a comparative overview of potential service providers, highlighting their expertise, experience, and certifications.
| Provider | Expertise | Experience (Years) | Certifications/Accreditations |
|---|---|---|---|
| Example Provider 1 | Information Security Management Systems (ISMS), Financial Services | 15 | ISO 19011, ISO 27001 Lead Implementer |
| Example Provider 2 | Healthcare, Manufacturing | 10 | ISO 27001 Lead Auditor, ISO 27005 Lead Implementer |
Note: This table provides examples; actual providers and their qualifications may vary. Thorough research and due diligence are essential when selecting a service provider.
Common Challenges and Solutions in ISO 27001 Certification

Successfully navigating the ISO 27001 certification process often presents specific challenges. Understanding these hurdles and implementing effective solutions is crucial for a smooth and ultimately successful outcome. This section will explore common obstacles and offer practical strategies for overcoming them.
The ISO 27001 standard, while providing a robust framework for information security management, requires significant organizational commitment and effort. Challenges can arise from various aspects of the process, including initial assessment, implementation, and ongoing maintenance.
Initial Assessment Challenges
Many organizations struggle with accurately identifying their current information security risks and controls during the initial assessment phase. This often stems from a lack of clear documentation, inadequate understanding of the standard, or insufficient internal communication. Thorough risk assessments are essential for a strong foundation. Organizations should utilize established risk assessment methodologies and leverage expertise from experienced consultants to identify potential vulnerabilities and align them with the standard. This will allow for a comprehensive evaluation of existing practices, identifying strengths and weaknesses.
Implementation Challenges
Implementing the required controls can be challenging due to resource constraints, resistance to change from employees, or lack of clear communication. Effective communication and training are key to gaining employee buy-in. Clear communication about the reasons for the changes and the benefits of compliance will significantly reduce resistance. Developing a phased implementation plan allows organizations to manage resources effectively and ensures that the transition does not overwhelm the workforce.
Maintaining Certification, Iso 27001 certification services
Sustaining ISO 27001 certification requires ongoing vigilance and adherence to the standard. A key challenge lies in maintaining a consistent level of control throughout the organization. Regular internal audits are vital for identifying and addressing gaps. Continuous monitoring of the implemented controls and periodic review of the ISMS (Information Security Management System) are crucial to ensure ongoing compliance.
Risk Management Strategies
Effective risk management is paramount throughout the certification process. Organizations should establish a clear risk assessment framework, documented procedures, and well-defined roles and responsibilities. The risk register should be regularly reviewed and updated to reflect changing circumstances. This ongoing monitoring ensures that the ISMS remains relevant and effective.
Key Considerations for Successful Certification
“Document all procedures, ensure internal buy-in, and stay updated on changes to the ISO 27001 standard.”
These best practices, when followed diligently, contribute significantly to a smooth and successful certification journey. Comprehensive documentation of procedures ensures accountability and traceability. Internal buy-in fosters a culture of compliance and facilitates smoother implementation. Regularly reviewing the standard ensures that the ISMS remains aligned with the latest requirements. Implementing these key considerations will ultimately lead to successful certification.
Cost and Time Estimation for ISO 27001 Certification Services
Accurately estimating the cost and timeframe for ISO 27001 certification is crucial for organizations planning this process. A thorough understanding of the influencing factors and a clear pricing model are essential for effective budgeting and project management. Proper planning minimizes potential surprises and allows for a smoother transition to compliance.
A well-defined scope, the complexity of the organization’s existing security controls, and the experience of the chosen certification body all significantly impact the final cost and timeline. The availability of internal resources also plays a pivotal role in determining the overall duration and associated expenses.
Factors Influencing Certification Costs
Several key factors influence the cost of ISO 27001 certification services. The size and complexity of the organization are major determinants. Larger organizations with extensive operations and intricate processes typically require more time and resources for assessment and implementation, leading to higher costs. The current security posture of the organization also plays a role. Organizations with robust existing security controls may require less extensive modifications, potentially leading to lower costs. The chosen service provider, their expertise, and the scope of services offered will also significantly affect the final price. Finally, geographical location and specific requirements of the organization can influence the cost.
Framework for Cost and Timeline Estimation
A structured approach to estimating the cost and timeline for ISO 27001 certification is essential. The first step involves clearly defining the scope of the certification process. This includes identifying all relevant departments and systems to be included. Next, evaluate the current security posture and identify gaps between the organization’s existing practices and the requirements of ISO 27001. Determining the required resources, including internal personnel and external consultants, is crucial for accurate cost estimation. This evaluation helps determine the required training and support, which is often a significant component of the overall cost. Finally, consider the time required for gap analysis, documentation, implementation, and the certification audit itself.
Pricing Models for ISO 27001 Certification Services
Various pricing models are employed by ISO 27001 certification service providers. Some providers offer fixed-price packages for organizations with a well-defined scope and a relatively simple implementation process. Other providers may use an hourly rate for consulting services, allowing for more flexibility in addressing specific organizational needs. Some organizations offer tiered packages, offering varying levels of support and resources for different organizational sizes and needs.
Cost Breakdown for ISO 27001 Certification
The following table provides a general overview of cost breakdowns for ISO 27001 certification, highlighting different cost categories, their estimated costs, and approximate timelines. This table is a general guide, and actual costs will vary depending on specific organizational needs and circumstances.
| Category | Cost (Estimated) | Timeline (Estimated) |
|---|---|---|
| Gap Analysis and Assessment | $3,000 – $15,000 | 2-4 weeks |
| Policy and Procedure Development | $2,000 – $8,000 | 2-4 weeks |
| Implementation of Controls | $5,000 – $25,000+ | 4-8 weeks |
| Internal Audit Support | $1,000 – $5,000 | 1-2 weeks |
| Certification Audit Fee | $2,000 – $10,000 | 1-2 weeks |
| Total (estimated range) | $13,000 – $63,000+ | 2-12 weeks |
Case Studies and Success Stories: Iso 27001 Certification Services
Real-world examples illuminate the tangible benefits of ISO 27001 certification. Organizations across diverse sectors have successfully implemented these frameworks, achieving significant improvements in security posture and operational efficiency. Understanding these success stories provides valuable insights for organizations considering similar initiatives.
Illustrative Examples of Successful Implementations
Various organizations have demonstrated the positive impact of ISO 27001 certification. These cases showcase how the framework can address specific challenges and lead to tangible results. The following examples highlight successful implementations, demonstrating the wide applicability of the standard.
Table of Successful ISO 27001 Implementations
This table provides a concise overview of several successful ISO 27001 implementations. It illustrates how organizations tackled specific challenges, adopted tailored solutions, and ultimately achieved quantifiable results.
| Organization | Challenges | Solutions | Results |
|---|---|---|---|
| SecureData Inc. (Fictional) | Scattered security policies and procedures, leading to inconsistent application across departments. High employee turnover contributed to knowledge gaps in security best practices. Difficulty in maintaining compliance with evolving regulatory requirements. | Developed a comprehensive, centralized security policy document. Implemented a structured training program for all employees on security best practices, covering both basic and advanced aspects. Established a dedicated team responsible for ongoing monitoring and improvement of security controls, including regular reviews of regulatory changes. Used a risk management framework to proactively identify and address potential security threats. | Significant reduction in security incidents. Improved employee awareness and adherence to security protocols. Streamlined internal audit processes and achieved faster regulatory compliance. Stronger overall security posture. Enhanced reputation for security and compliance with clients and partners. |
| GlobalTech Solutions (Fictional) | Lack of a robust incident response plan. Inefficient communication channels between security teams and other departments during security breaches. Difficulty in detecting and responding to advanced persistent threats (APTs). | Developed a detailed incident response plan, including roles and responsibilities, communication protocols, and escalation procedures. Established a dedicated incident response team. Implemented security information and event management (SIEM) tools to enhance threat detection capabilities. Provided security awareness training to all employees. Developed partnerships with external security experts for incident response support. | Improved response time to security incidents. Reduced the impact of security breaches on business operations. Enhanced the organization’s ability to identify and mitigate threats. Improved collaboration and communication between different departments. |
| FinCorp Bank (Fictional) | Difficulty in complying with stringent financial regulations concerning data security. Concerns about regulatory penalties for data breaches. Increased cyber threats targeting financial institutions. | Implemented a comprehensive data security framework that aligned with relevant financial regulations. Established a dedicated data security team. Developed detailed procedures for handling customer data. Implemented advanced security controls, such as multi-factor authentication and encryption. Underwent regular security assessments and penetration testing. | Improved compliance with financial regulations. Reduced the risk of regulatory penalties. Stronger security posture to mitigate cyber threats. Improved reputation for data security and trust among customers. |
Final Review
In conclusion, ISO 27001 certification services are crucial for organizations seeking to enhance their information security. Careful consideration of provider expertise, service offerings, and cost structures is essential for a successful implementation. By understanding the process and potential challenges, organizations can proactively mitigate risks and build a robust security framework. The certification paths are paved with meticulous planning, consistent effort, and a commitment to continuous improvement.